As I haven't written a post for a while, I thought I would get back into practice by writing a technical troubleshooting one for an issue I have recently had to content with. So here it goes.
So what's this all about?
I have recently deployed an Azure Virtual Desktop environment into my lab, to get a feeling for the AzureAD joined experience. There are a whole host of caveats listed by Microsoft including shared user profiles, fslogix streaming and various other bits... so needed to validate them.
After spinning everything up, I was able to log in to my host pool using the Remote Desktop client installed on my AzureAD joined laptop with Windows Hello... it worked beautifully!
However, I then tried to connect using the web client, android, iPad and even a none AAD joined device. When I tried, I simply got an error stating 'Username or Password did not work'. Confusing as hell!
How did I troubleshoot this?
So, how did I fix it. First, I ran through the various pre-reqs to make sure I hadn't missed a step. This is a great post to run through: Deploy Azure AD joined VMs in Azure Virtual Desktop - Azure | Microsoft Docs
Some points that I had completed:
- Added the targetisaadjoined:i:1 to the custom RDP Properties on my host pool.
- Disabled 'per-user' legacy MFA for any users wanting to connect.
- Ensured the Conditional Access Policy was configured as expected.
- Ensured that I had added the users to a group that had 'Virtual Machine User Login' on the IAM tab for the host pool.
Guess what? None of the above worked... I was still getting the same error! So, time to troubleshoot in more detail.
Easiest way to do that is to use the RDWeb portal, and enable logging. This is done by clicking on the burger button (top right), and choosing about:
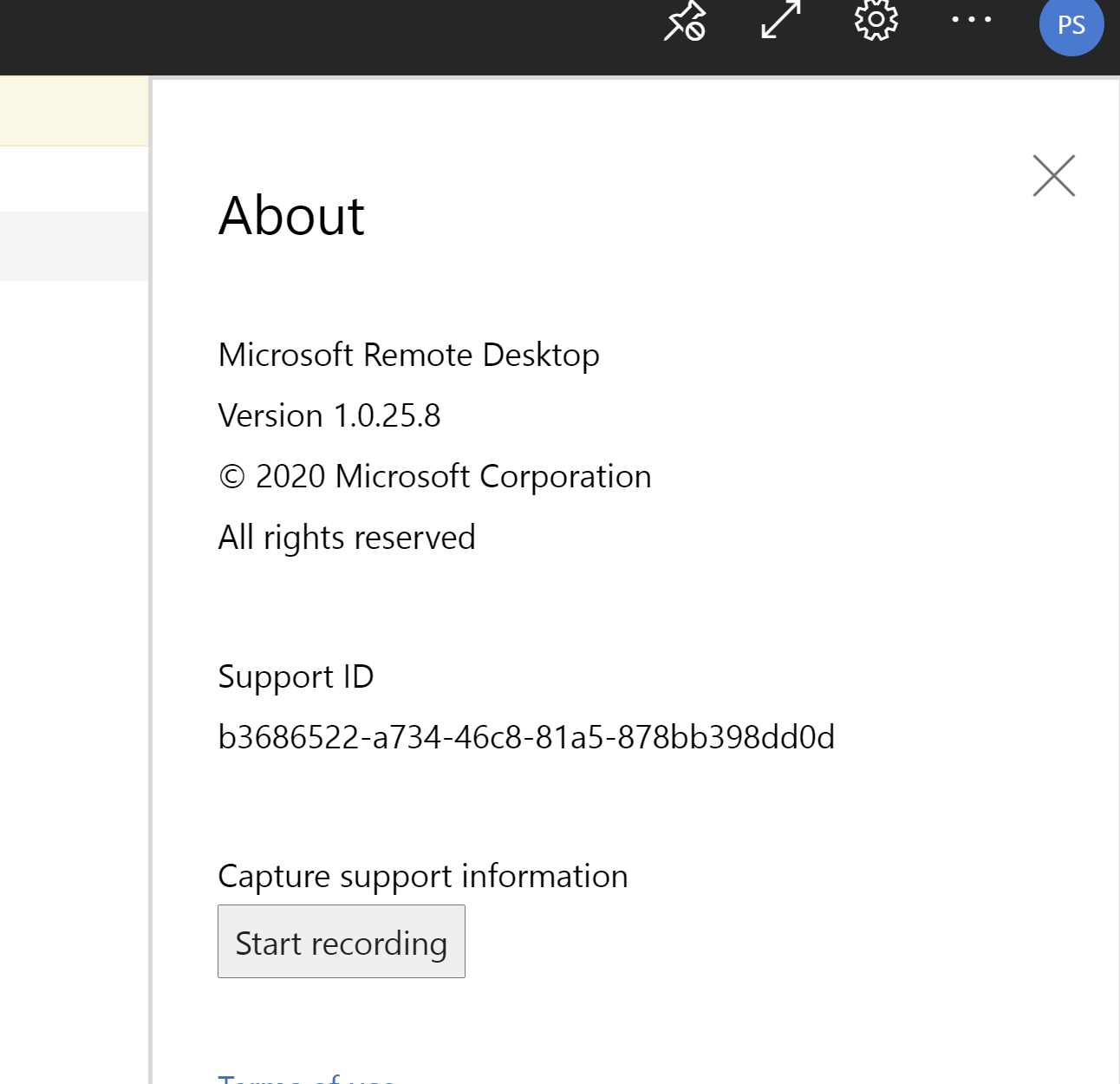
You can then see 'Start Recording'. Then run through the login process, and stop recording. It will download you a txt file with the error trace.
Looking through the logs, I was seeing an RDSTLS error:
The server reported an error during RDSTLS authentication, error code=1326
So it was something to do with passing the authentication through the non-AAD joined devices.
Time for the resolution!
So to resolve, I ended up adding the enterprise application 'Azure Windows VM Sign-in' as an exclusion to my Conditional Access policy:
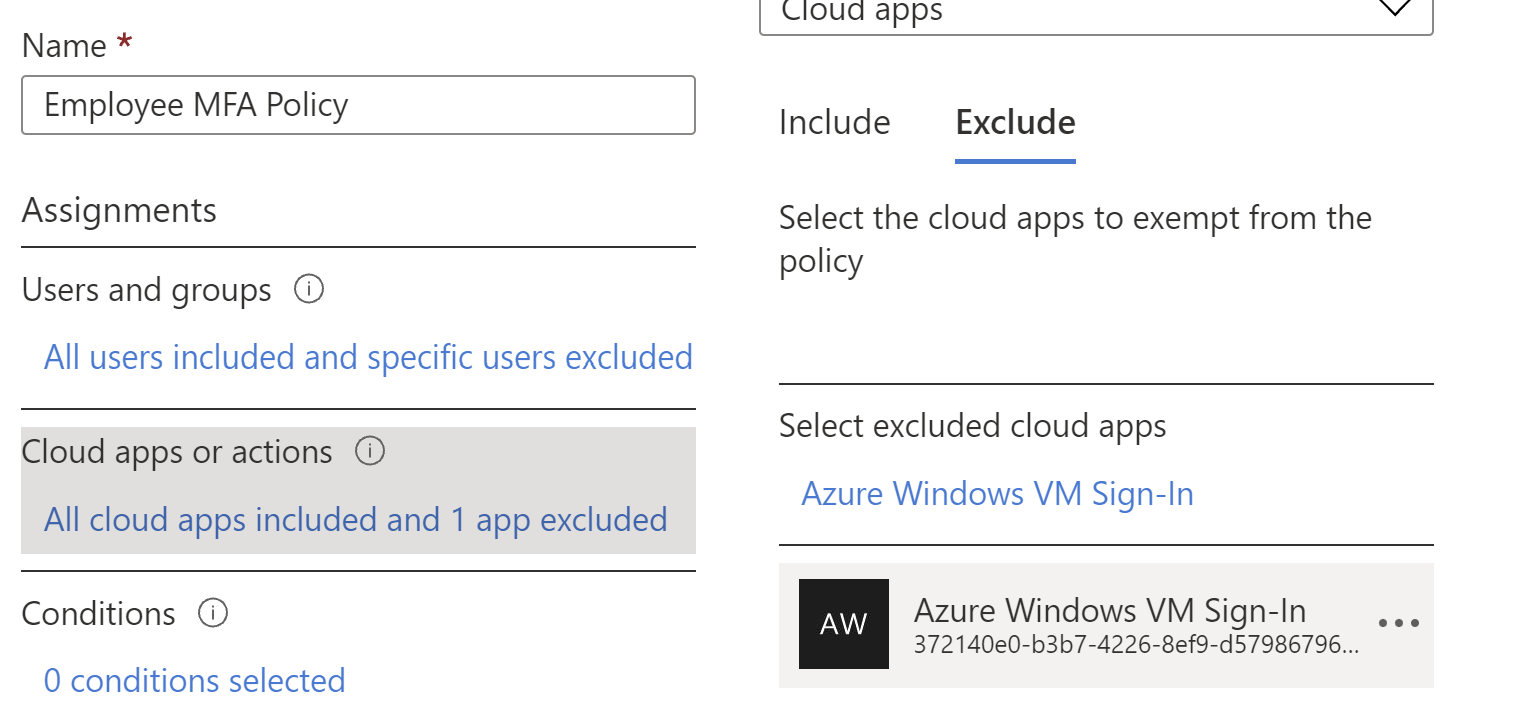
And there we go, I was able to successfully login from non-AAD joined devices.
Now, what is the impact?
From what I can tell, this enterprise application only applies to the secondary login box once you have already passed MFA when loading your session host. So you are still protected by the CA policy, it is just the 'windows login' that requires username and password.
Hope this helps someone!
